Better Apps Through Better Privacy
Better Apps Through Better Privacy
WWDC 2018
Privacy Is About People
- Build trust with your users
- Respect users in handling their data
- Apply privacy thinking to engineering decisions
Ask Questions about Data
- Why do we need this data ?
- Would this surprise our users ?
- Could we use less granular data ?
- How long do we need this data ?


Recognize Data Assumptions 😡
- “Of course we should log this for all users.”
- “This data couldn’t possibly be sensitive.”
- “It’s fine to apply this data in a new use case.”
- “There’s no PII, so don’t worry about it.”
- “We already protect this with encryption.”
Create Privacy Guarantees 😆
- Write high-level statements about privacy expectations
- Decide in planning, verify in implementation
- Examples:
- “We can’t read your messages in transit between devices.”
- “Analytics data doesn’t identify you personally.”
- “We only retain aggregate usage data.”
Handle Data with Caution
- Data brings power 💪 — and danger ⚠️
- Gathering data adds overhead and liability
- Unexpected data adds more risks and distrust

Use Proportional Data Collection
- Collect only what is needed to achieve the goal
- Collect consistently with user expectations
- Don’t collect without a clear reason 😱
Use Privacy Techniques
- Develop a toolbox
- Adjust to match use case
- Apply across systems
- Build technical enforcements
Big Ideas to Remember
- Privacy is about people
- Ask the “should” questions
- Align data practices with use cases
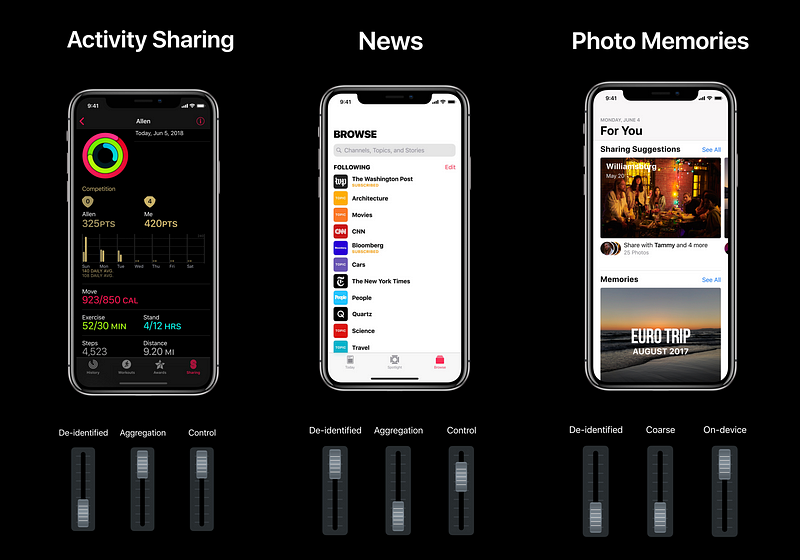
Building Privacy in Your App
- Accessing User Data
- Data Stewardship
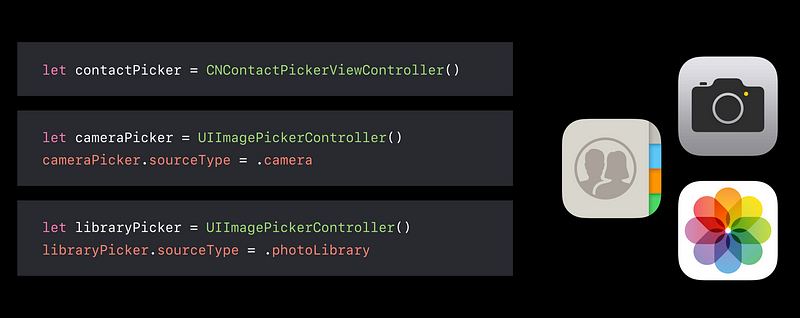
Use Out-of-Process Pickers
- Available for Contacts, Camera, and Photos
- Will not trigger a permission prompt
- Default method for accessing data
Protected Resources

Requesting Access
- Only what you need
- Only when you need it
- Only rely on the API for status
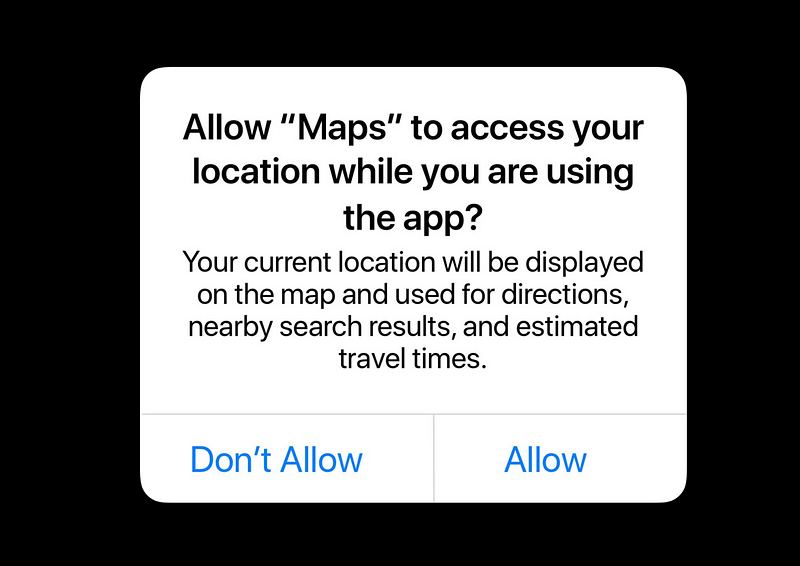
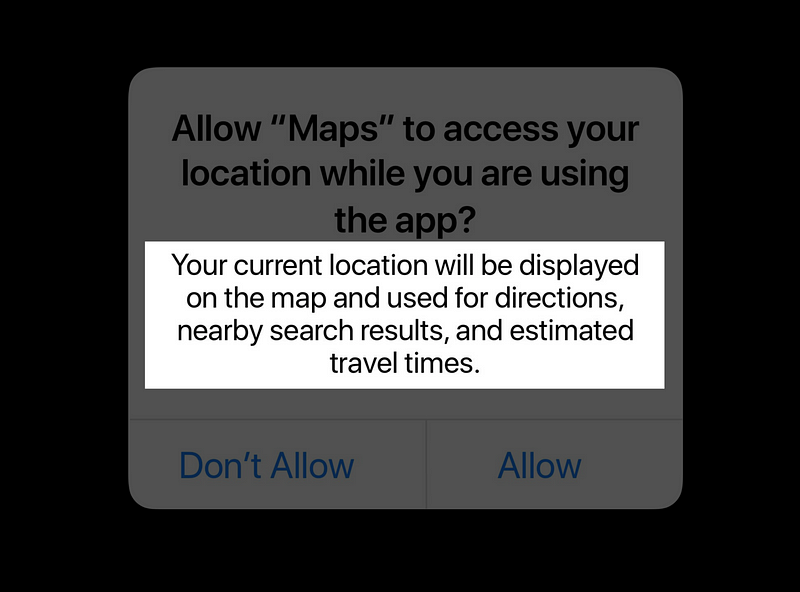
Include Purpose Strings
- Required for requesting access
- One method for transparency
- Explains the reason for a request
Unhelpful Purpose Strings 😡
- “”
- “_”
- “true”
- “NSLocationAlwaysUsageDescription”
- “Advertising”
- “This app requires location”
- “Used to provide you more relevant content”
Helpful Purpose Strings 😊
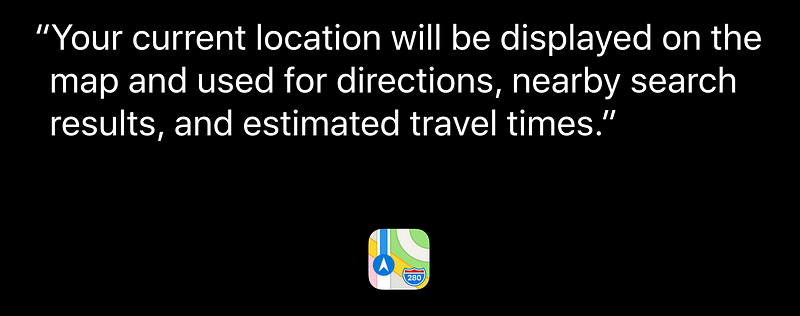
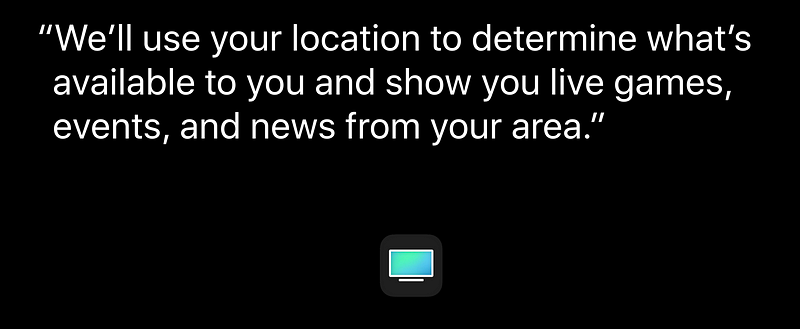

Managing Access
- Apps should not require access to protected resources
- Build fallbacks if user declines access
- Verify in case user revokes access
- Stay aware of 3rd-party SDKs
- Provide ongoing transparency
WiFi Network Information (new)
- Now requires AccessWiFiInformation capability
- Used to check if an accessory is on the network
- Enable only when necessary for your use case
Health Records (new)
Protected Resources (new)

Protected Resources (new)
- Access to resources may now trigger a prompt
- Prompts apply to any 3rd-party app process
- Includes apps outside the App Store
- Purpose strings will be required
- Your Apps and the Future of macOS Security ( WWD 2018 )
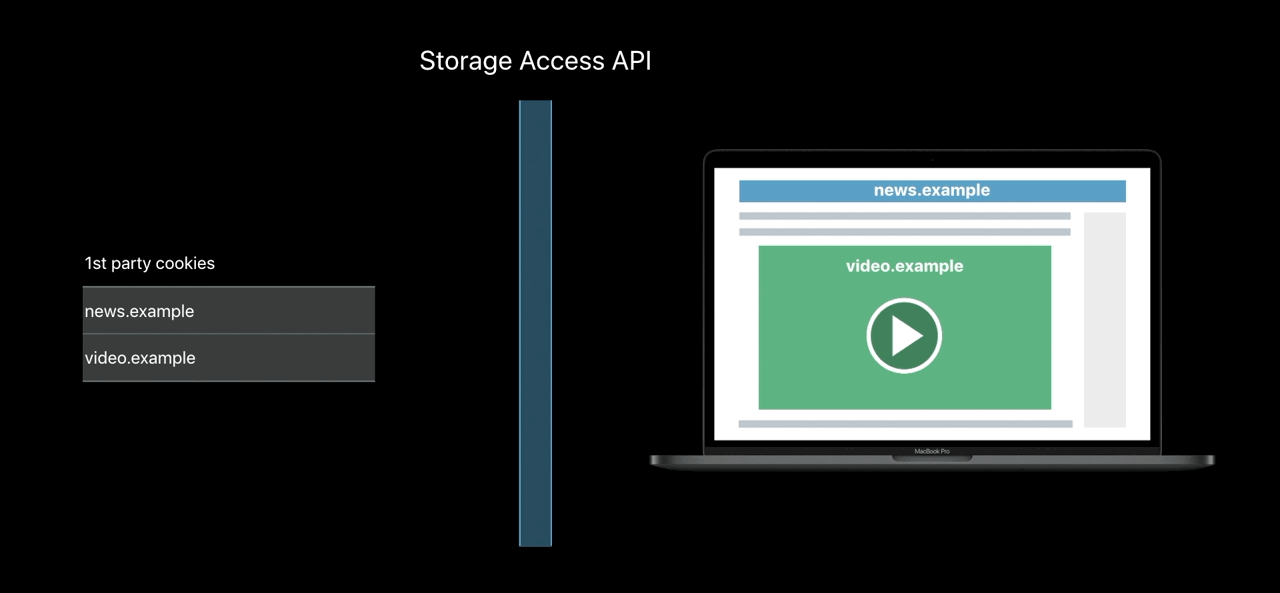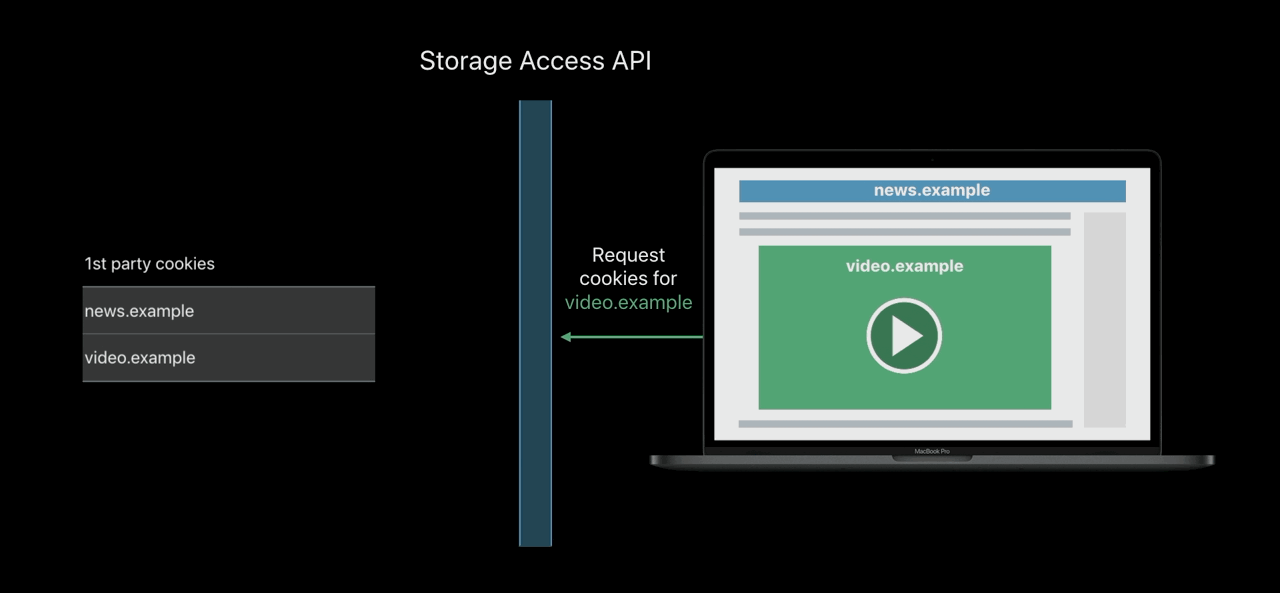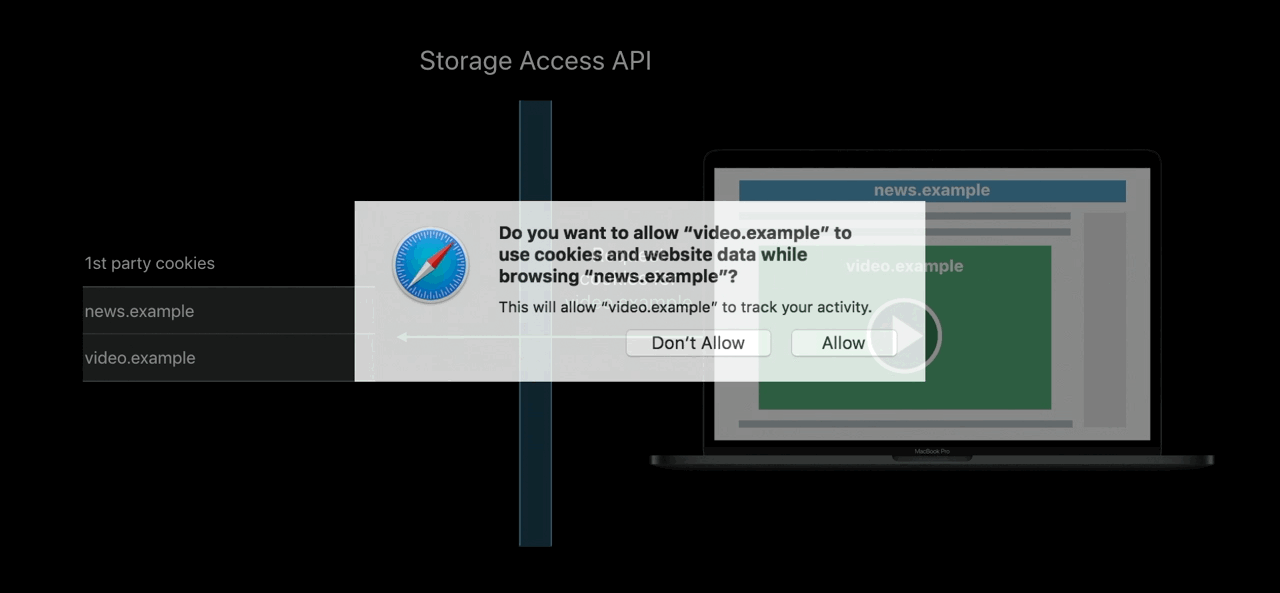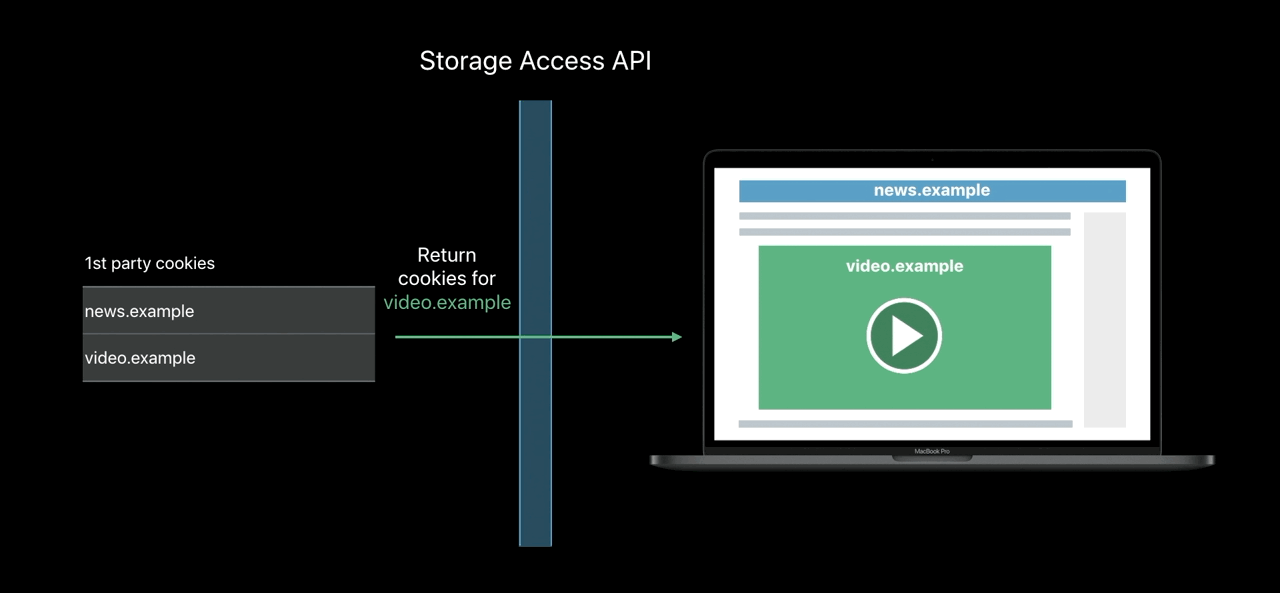
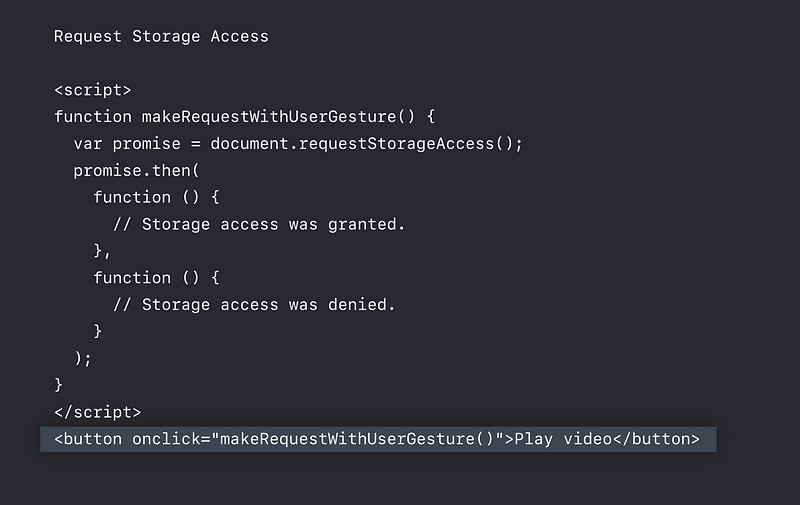
Storage Access API
- Engage with logged-in content from embedded 3rd — parties
- Including from domains classified as trackers
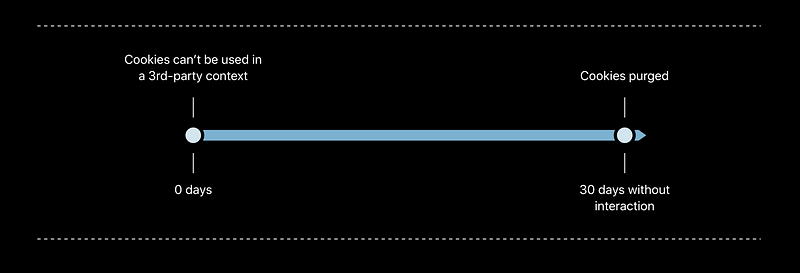
Intelligent Tracking Prevention 2.0
Cookies from domains classified as trackers partitioned immediately
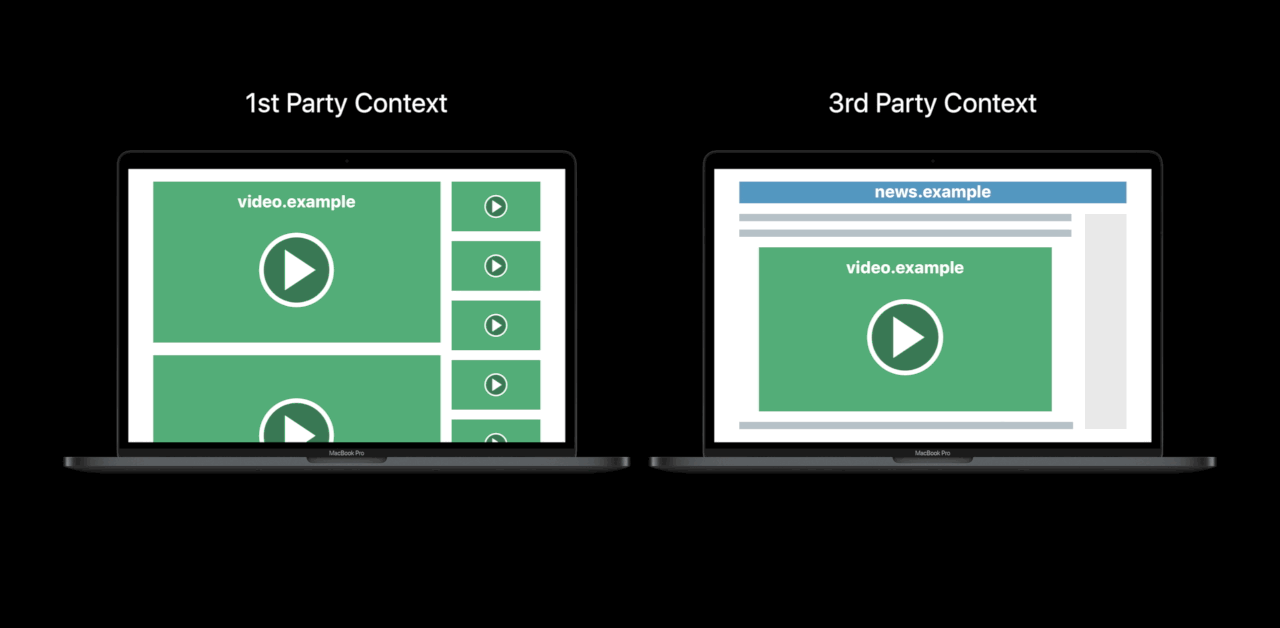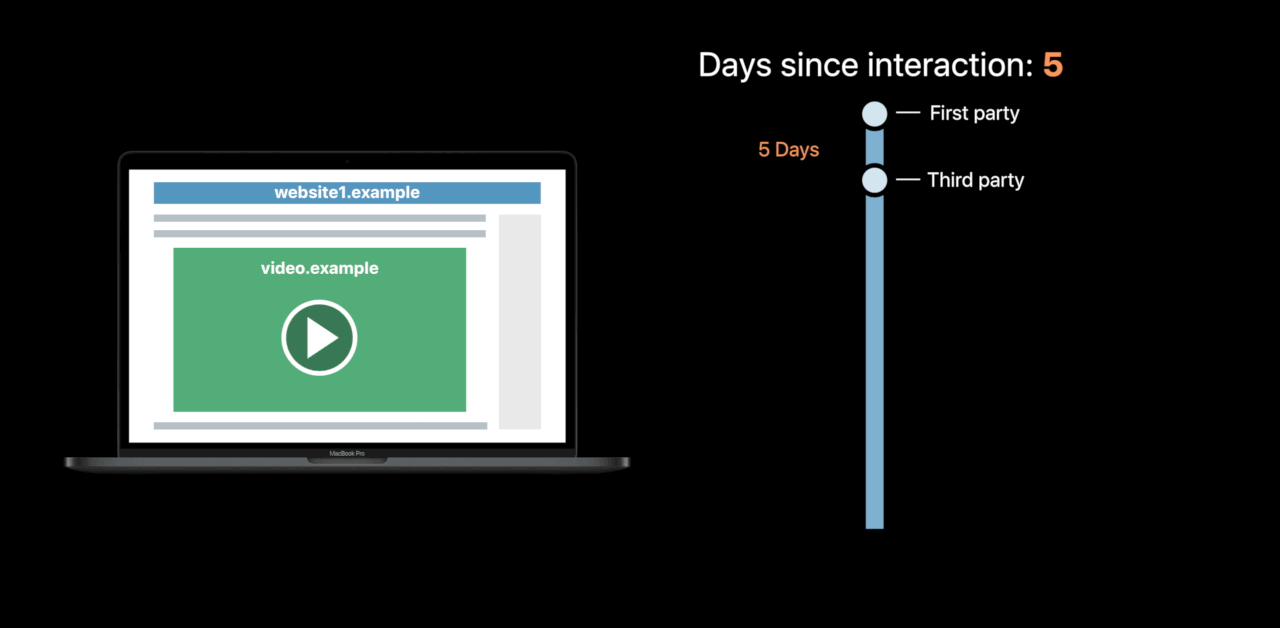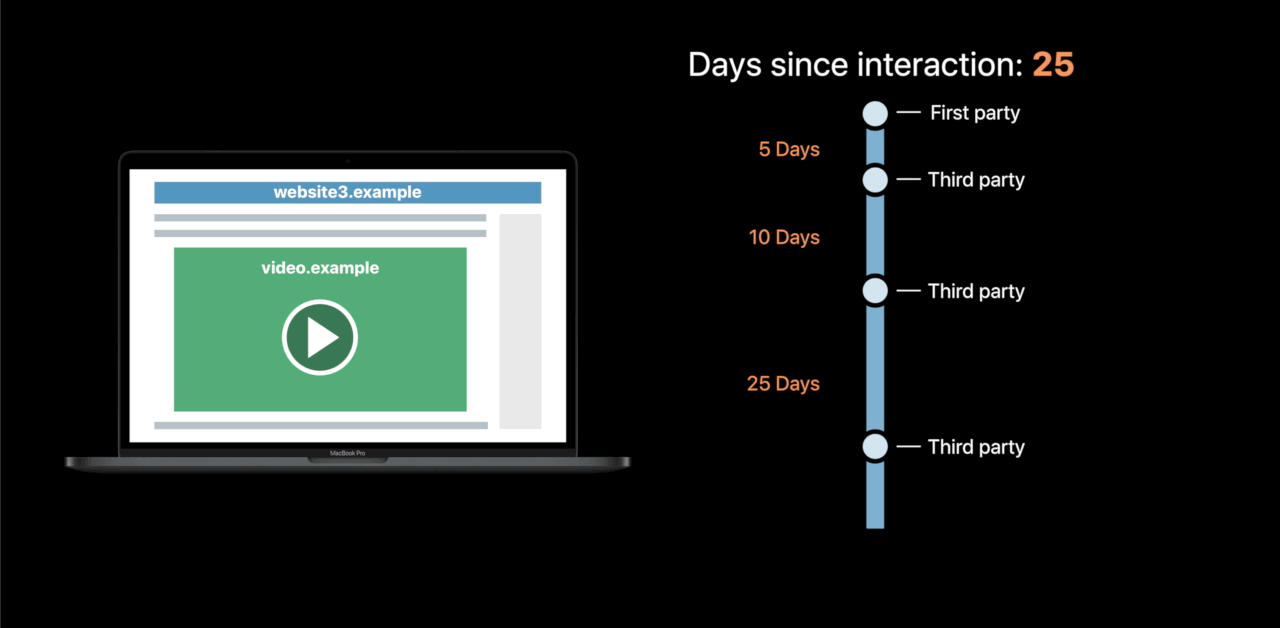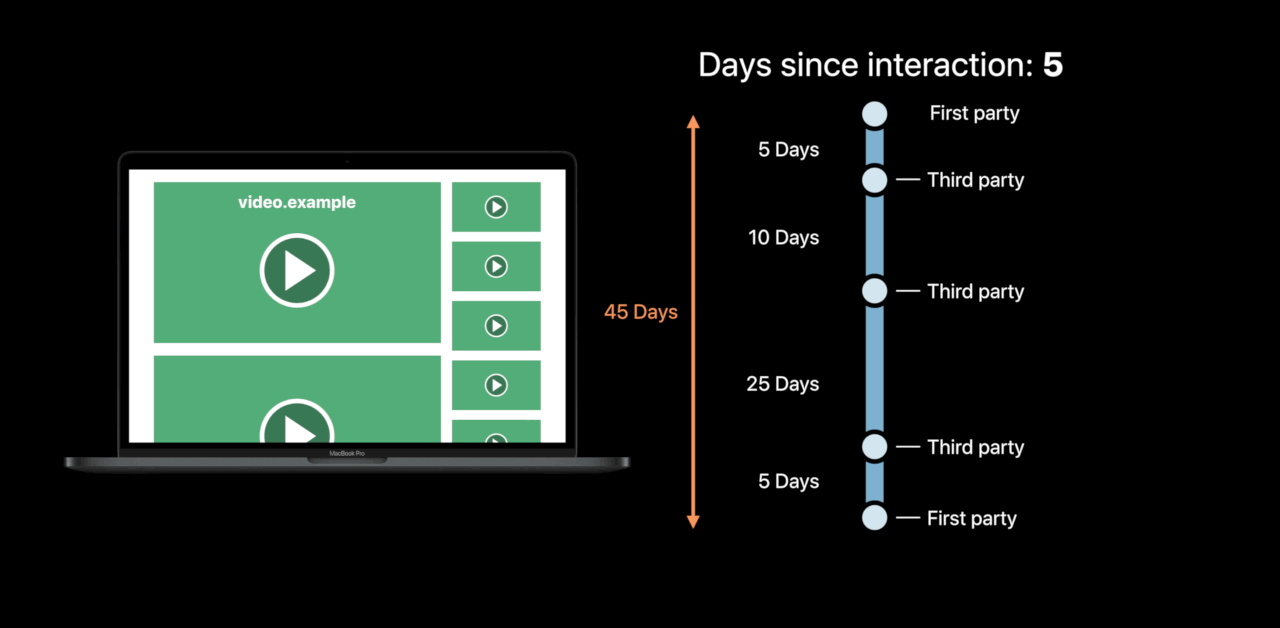
Data Stewardship
- Deletion
- Device Tracking
- 3rd-Party Partners
- Machine Learning
Clean Up Deleted Data
- Recognize data flow going outside your app
- Ensure consistency across systems
- Update data shared with Operating System
- Siri Shortcuts
- Notifications
- Passwords

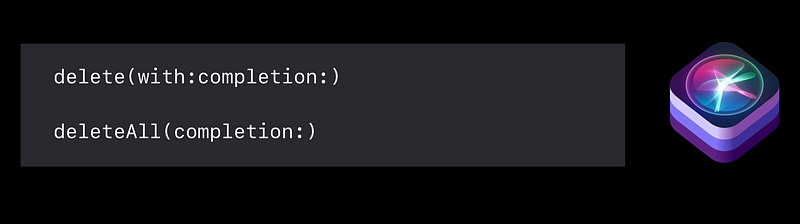
Siri Shortcuts
INInteraction
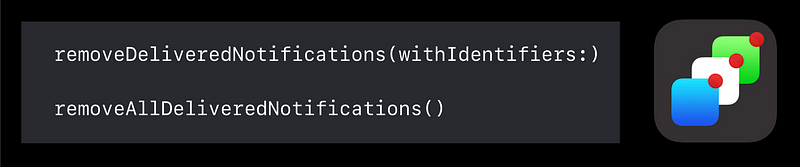
Notifications
UNUserNotificationCenter
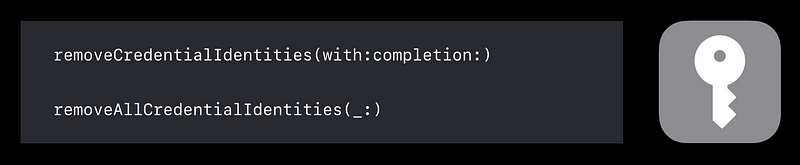
Passwords
ASCredentialIdentityStore
Device Tracking
You Might Want to Know…
- Did this device already consume a free trial ?
- Has this device paid for content but not linked that purchase to an account ?
- Was this device previously used by an abusive user ?
- Was this device previously used for fraudulent activities ?
DeviceCheck
- Set 2 bits of data per device
- Stored by Apple with timestamp
- Persist across reset or erase install
- Do not rely on unsupported device tracking methods
- Continuing to remove entropy (unique device attributes)
- Continuing to remove functionality being abused to uniquely identify users
3rd-Party Code
- You’re responsible for all code in your app
- Understand data access or transfers
- Be complete when giving transparency
- Avoid unnecessary requests for resources
3rd-Party Vendors
- Data flow to 3rd parties from yours servers
- Know your partners’ data practices
- Be transparent about all use cases
Face ID
- Built with privacy-friendly machine learning
- Easy to add Face ID authentication to your app
- Use the LocalAuthentication framework

ARKit 2
- Uses machine learning to model the environment
- Create, persist, and share map of environment
- Collect this map only if needed for your feature
- Use MultipeerConnectivity API for end-to-end encryption

Create ML + Core ML 2
- Easier than ever to add on-device machine learning to your app
- Train models on your Mac
- Evaluate models on your user’s device
- Avoid collecting sensitive user data
Does my model reveal training data ?
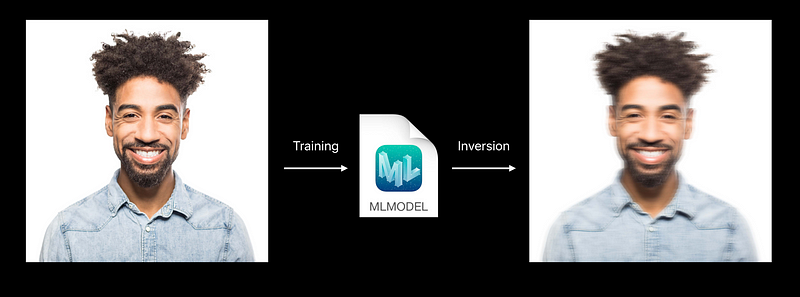
Can I infer more about my users than they expected?
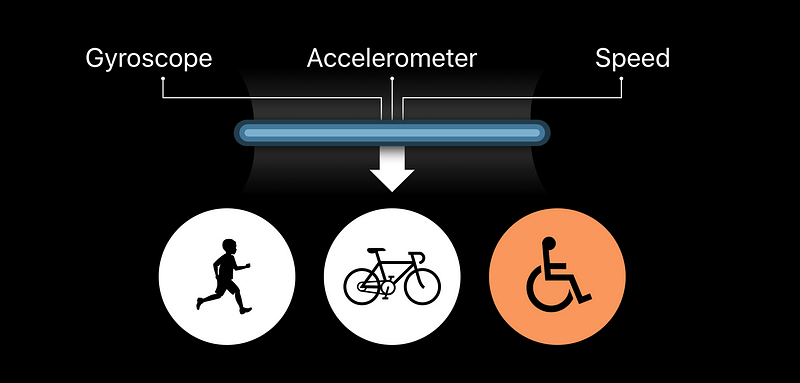
Mitigations
- Ensure you train on the right data
- Keep model complexity proportional to goal